Important aspects of SPF : –
The Sender Policy Framework (SPF) is an important email authentication protocol that helps prevent email spoofing and phishing attacks. Here are some key aspects to consider when setting up and managing SPF:
SPF Record: The SPF record is a DNS TXT record associated with your domain that specifies the authorized email servers (IP addresses or hostnames) allowed to send email on behalf of your domain. It contains the mechanisms and modifiers that define the rules for SPF checks.
Authorized Sending Sources: Identify and include the IP addresses or hostnames of the email servers that are authorized to send email on behalf of your domain in the SPF record. This ensures that legitimate email sources are properly authenticated.
Mechanisms: SPF uses mechanisms to define the authorized sending sources. Common mechanisms include “a” (authorizes the domain’s A record), “mx” (authorizes the domain’s MX record), “ip4” (authorizes specific IPv4 addresses), “ip6” (authorizes specific IPv6 addresses), and “include” (allows inclusion of another domain’s SPF record).
Soft Fail and Hard Fail: SPF provides two different results for SPF checks. “Soft Fail” (designated with the “~” symbol) indicates that the SPF check has failed but should be treated as a warning rather than a definitive reason for rejecting the email. “Hard Fail” (designated with the “-” symbol) indicates that the SPF check has failed, and the email should be rejected or flagged as suspicious.
Neutral and Pass: Besides soft fail and hard fail, SPF can also yield a “Neutral” result (designated with the “?” symbol), which indicates that the SPF check result is inconclusive. “Pass” (designated with the “+” symbol) indicates that the SPF check has succeeded, and the email is authorized.
Multiple SPF Records: It’s important to have only one valid SPF record per domain. Multiple SPF records can cause conflicts and lead to unpredictable SPF check results. If you need to combine multiple sources, use the “include” mechanism to include the SPF records of the authorized sources.
DNS Propagation: After making changes to your SPF record, allow time for the DNS changes to propagate. DNS propagation can take up to 48 hours, during which the updated SPF record may not be immediately recognized by all email servers.
Monitoring and Maintenance: Regularly monitor your SPF record for any changes in authorized sending sources. Update the SPF record as necessary to reflect changes in your email infrastructure, such as adding or removing email servers or IP addresses.
How does SPF Record work?
Now that you have the big picture behind SPF, let’s look at an SPF policy in action and see how the process unfolds:
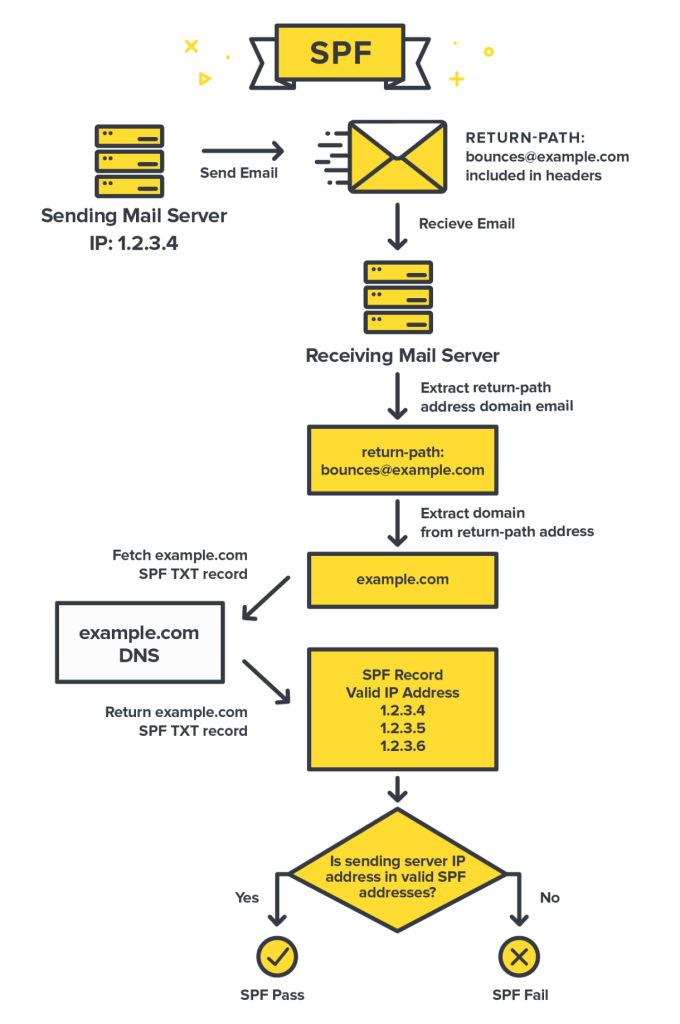
At a high level, here is the workflow of how a mail server checks SPF:
- The server with the IP address of 1.2.3.4 sends an email, and that email is using [email protected] as the Return-Path.
- The receiving mail server grabs the Return-Path domain and checks out the domain’s DNS records for example.com, looking for the SPF record.
- The receiving server found the SPF record for example.com! Now, it checks if any of the IP addresses listed as valid senders for the domain match the address that was used to send the email.
- In this example, it’s a match! The sending IP 1.2.3.4 is listed as an approved sender, so SPF passes. ✅ If the IP addresses don’t match, that would cause SPF to fail. This would likely make the receiving server suspicious, and they might reject the mail.
SPF record syntax and its breakdown: –

SPF record syntax might look complicated and confusing at first, but it is fairly easy to understand once you know the basics.
Let’s look at a breakdown of the key elements (also called “mechanisms”) in an example SPF record entry of v=spf1 a mx include:spf.mtasv.net include:_spf.createsend.com ~all.
The first thing to note is the syntax of the SPF record. It’s broken down into the version prefix and one or more mechanisms:
The version prefix is pretty simple. Since there can be multiple TXT records for a domain, this is the way to let parsers know that this is the record to be used for SPF checking.
The second part of the SPF record are the mechanisms. These specify different rules on how to check for SPF.
What are SPF qualifiers?
The mechanisms can also have a prefix that describes the action to take when a sending IP matches the qualifier. The default qualifier is +. So the Postmark SPF record is the same as:

Let’s go over what qualifiers are available.
- + Pass, an IP that matches a mechanism with this qualifier will pass SPF.
- – Fail, an IP that matches a mechanism with this qualifier will fail SPF.
- ~ SoftFail, an IP that matches a mechanism with this qualifier will soft fail SPF, which means that the host should accept the mail, but mark it as an SPF failure.
- ? Neutral, an IP that matches a mechanism with this qualifier will neither pass or fail SPF.
The “a” mechanism
Let’s say that I send mail from IP 1.2.3.4 for the domain “example.com.” If “example.com” has an A record that returns 1.2.3.4 then this mechanism will pass.
The “mx” mechanism
Any domain that hosts email has one or more mx records. These records define which email servers can relay email. For instance, when using Google Apps, you insert several MX records into DNS. Including the “mx” mechanism automatically approves these servers and avoids you having to list them individually. This also prevents maintaining the list if they change later.
The “include” mechanism
Let’s say that I send mail from IP 1.2.3.4 for the domain “example.com.” If the SPF record for “example.com” includes spf.mtasv.net and 1.2.3.4 passes against the SPF record for spf.mtasv.net, this mechanism will pass.
The “all” mechanism
The “all” mechanism will match against everything, and in this case, the result will be a SoftFail for everything that gets to this point.
How to check your SPF Records?
- Terminal on your local machine: –
“dig” command on MacOS/Linux — > dig mail.salesforce.com TXT (for text records)
“nslookup” command on Windows/MacOS/Linux — > nslookup –type=txt mail.salesforce.com (for text records)
- Online Tools: –
DNS Checker
Mimecast
AccuWeb Hosting
By paying attention to these important aspects, you can properly configure and maintain your SPF record, enhancing email deliverability, reducing the risk of email spoofing, and improving the overall security of your email communications.
For more information related to SFMC, please reach out to us on our website genetrix.tech or simply write to us at [email protected]